Sun Tzu said: Raising a host of a hundred thousand men and engaging them in war entails heavy loss on the people and a drain on the resources. The daily expenditure will amount to a thousand ounces of silver. There will be commotion at home and abroad, and men will drop out exhausted. Opposing forces may face each other for years, striving for the victory which may be decided in a single day. This being so, to remain in ignorance of the enemy’s condition simply because one grudges the outlay of a hundred ounces of silver is the height of stupidity. One who acts thus is no leader of men, no present help to his cause, no master of victory. Thus, what enables the wise commander to strike and conquer, and achieve things beyond the reach of ordinary men, is foreknowledge. Now this foreknowledge cannot be elicited from spirits; it cannot be obtained inductively from experience, nor by any deductive calculation. Knowledge of the enemy’s dispositions can only be obtained from other men. Hence the use of spies, of whom there are five classes: (1) Local spies — Having local spies means employing the services of the inhabitants of an enemy territory; (2) Moles — Having moles means making use of officials of the enemy; (3) Double agents — Having double agents means getting hold of the enemy’s spies and using them for our own purposes; (4) Doomed spies — Having doomed spies means doing certain things openly for purposes of deception, and allowing our spies to know of them and report them to the enemy; (5) Surviving spies — Surviving spies means are those who bring back news from the enemy’s camp. When these five kinds of spy are all at work, none can discover the secret system. This is called “divine manipulation of the threads”. It is the commander’s most precious faculty. Hence it is that which none in the whole army are more intimate relations to be maintained than with spies. None should be more liberally rewarded. In no other fields should greater secrecy be preserved. (1) Spies cannot be usefully employed without a certain intuitive sagacity; (2) They cannot be properly managed without benevolence and straight forwardness; (3) Without subtle ingenuity of mind, one cannot make certain of the truth of their reports; (4) Be subtle! be subtle! and use your spies for every kind of warfare; (5) If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death together with the man to whom the secret was told. Whether the object be to crush an enemy, to storm a territory, or to kill an enemy general, it is always necessary to begin by finding out the names of the attendants, the aides-de-camp, and door-keepers and sentries of the general in command. Our spies must be commissioned to ascertain these. The enemy’s spies who have come to spy on us must be sought out, tempted with bribes, led away and comfortably housed. Thus they will become double agents and available for our service. It is through the information brought by the double agent that we are able to acquire and employ local and inward spies. It is owing to his information, again, that we can cause the doomed spy to carry false tidings to the enemy. Lastly, it is by his information that the surviving spy can be used on appointed occasions. The end and aim of spying in all its five varieties is knowledge of the enemy; and this knowledge can only be derived, in the first instance, from the double agent . Hence it is essential that the double agent be treated with the utmost liberality. Hence it is only the enlightened and wise general who will use the highest intelligence of the army for purposes of spying and thereby they achieve great results. Spies are the most important asset, because on them depends an army’s ability to march. Link to PDF: GitHub
Showing posts with label Cyber Security. Show all posts
Showing posts with label Cyber Security. Show all posts
Sunday, May 30, 2021
The Use of Spies (by Sun Tzu)
Friday, May 21, 2021
Activating MFA on GitHub and also PAT [May 2021]
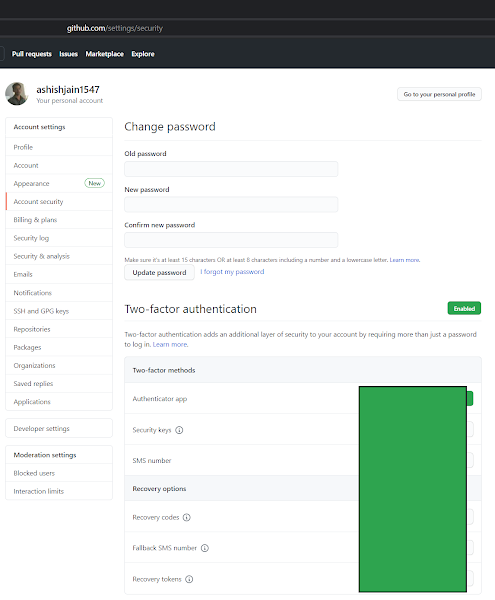
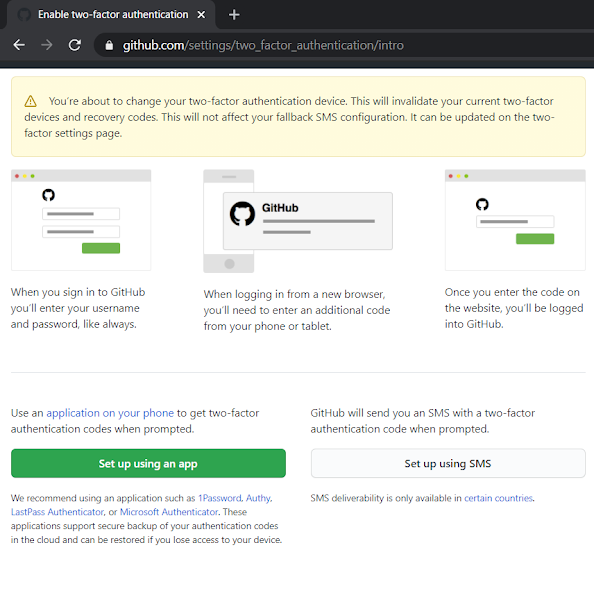
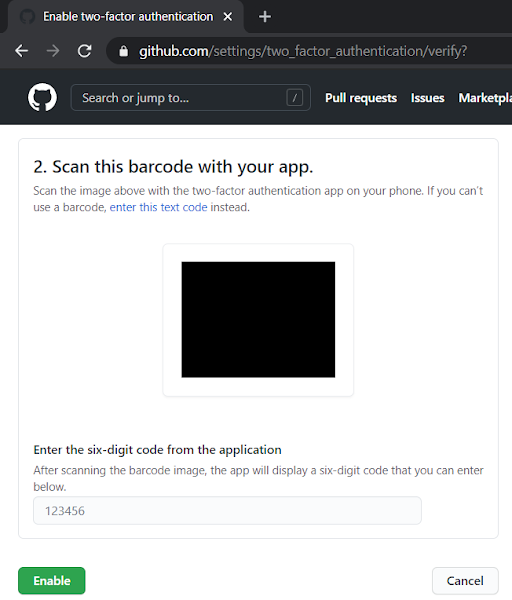
Log into GitHub account and follow the screenshots: I1 - Go to Account Security: github.com/settings/security I2 - GitHub MFA using Authenticator App I3 - GitHub asks you to scan a barcode and provide 6-digit code from the Authenticator app I4 - Microsoft Authenticator App (Download Screenshot) I5 - Manage MFA - Recovery Options [URL: github.com/settings/two_factor_authentication/configure ] I6 - Also make sure to set up: Personal Access Tokens [URL: github.com/settings/tokens] Tags: Cloud, Cyber Security, Technology,GitHub,
Activating MFA on Heroku (May 2021)
1 - MFA on Heroku (a Salesforce company) 2 - Connect an Authenticator app 3 - Microsoft Authenticator App (Download Screenshot) 4 - Heroku screen after multifactor authentication is done Tags: Cyber Security,Cloud,Technology,
Thursday, May 20, 2021
Censorship in India, Torrenting and Tor Browser
We were looking for a 1997 movie "Good Will Hunting" in ".mp4" format because my Sony Bravia Smart TV does not accept some other video file formats such ".webm" (See more about "webm" in End Note) and see how we solved this problem: Note: Third link in top 10 results in Google search solved our requirement. I1 - Good Will Hunting - Google Search I2 - Magnet Link Site (The Second Link in Google Search Results) but it did not work. Downloaded some garbage video file that did not run in VLC media player. I3 - The garbage files being downloaded with 'second search result' in qBitTorrent I4 - The video file fails to open in VLC media player Important Note: Along with video file, a Windows Batch program (.bat file) was also downloaded. This is a very good indication that something is fishy about this magnet link and these files. I5 - first search result and censorship in India - ytstvmovies.xyz - failed to open in Firefox with Airtel connection I6 - first search result and censorship in India - ytstvmovies.xyz - failed to open in Chrome with Airtel connection I7 - first search result and censorship in India - ytstvmovies.xyz - failed to open in Tor with Airtel connection I8 - third search result and censorship in India - yifytorrentme - failed to open in Firefox with Airtel connection I9 - third search result and censorship in India - yifytorrentme.com - failed to open in Chrome with Airtel connection I10 - third search result and censorship overridden with Tor Browser - yifytorrentme.com - opened in Tor with Airtel connection I11 - yifytorrentme.com - Found the movie using Tor and do check the ads on the site (Do not click any) I12 - yifytorrentme.com - Download begins by copy-pasting the Magnet link in qBitEnd Note
WebM is an audiovisual media file format. It is primarily intended to offer a royalty-free alternative to use in the HTML5 video and the HTML5 audio elements. It has a sister project WebP for images. The development of the format is sponsored by Google, and the corresponding software is distributed under a BSD license. The WebM container is based on a profile of Matroska. WebM initially supported VP8 video and Vorbis audio streams. In 2013, it was updated to accommodate VP9 video and Opus audio. [ Ref 1 ] About WebM WebM is an open, royalty-free, media file format designed for the web. WebM defines the file container structure, video and audio formats. WebM files consist of video streams compressed with the VP8 or VP9 video codecs and audio streams compressed with the Vorbis or Opus audio codecs. The WebM file structure is based on the Matroska container. [ Ref 2 ] [ Ref 3 - YouTube ] Tags: Technology,Cyber Security,Indian Politics,Politics,Web Development,Web Scraping,
Monday, May 10, 2021
Want a virus, here's one (Ref # Microsoft Security Intelligence)
What is a PUA? A potentially unwanted program (PUP) or potentially unwanted application (PUA) is software that a user may perceive as unwanted. It is used as a subjective tagging criterion by security and parental control products. Such software may use an implementation that can compromise privacy or weaken the computer's security. 1 - Doing Google search for a movie torrent 2 - yifymovies.net homepage 3 - Entire homepage has an overlay like an invisible wall 4 - The magnet link which was not clickable earlier is now clickable with also the cursor hover effect 5 - The new window that opens when you click on magnet link behind the invisible wall 6 - Windows Defender Alerts That You Start Getting Now On 7 - The fake app opener redirection page and the anti-virus defender alert for it 8 - The real choose an application window (that is coming from the browser built-ins) 9 - When you launch the torrent, your anti-virus defender alerts you for unwanted software 10 - Defender found threats 11 - More description and file location from Defender 12 - Description of PUA on Microsoft Security Intelligence site [ Microsoft Security Intelligence ] 13 - Actual file that was detected as PUA 14 - Details after action by Defender 15 - After all this, my utorrent stopped working and was failing to uninstall too 16 - after forced delete by deleting files instead of using appwiz.cpl, the file association is still there Tags: Technology,Cyber Security,
Saturday, May 8, 2021
Polymorphism in Google Drive and Google Chrome (wrt Handling an Exe File)
Important Note: We are not trying to arrive at a very concrete conclusion or result here. The testing was done to identify the behavior of 'Google Drive' and 'Google Chrome' when 'Google Drive' thinks a file could be a virus. User1: This user is the original author of the file and has shared the folder with User2. 1 - incognito, no-user, two virus alerts 2 - incognito, no user - A virus was detected you can't download this file (gmat2.zip) 3 - incognito, User2, virus detected, can't download 4 - incognito, User2, polymorphism, cannot delete file in shared folder from other person 5 - normal view, User1, file with virus alert can still be downloaded from original author's account 6 - incognito, User2, different type of alert for an exe file that gdrive says could be virus but did not alert before 7 - incognito, User2, can't download file, enable third-party cookies for GDrive 8 - normal view, User1, original author can remove a file from folder shared by him 9 - inconito firefox, User2, potentially infected exe file not downloadable from incognito chrome is allowed to be downloaded here 10 - a view of gdrive trash of original author User1 with removed files 11 - incognito, User2, you do not get remove rights on a file but you do get remove rights on the entire directory shared with you 12 - Incognito chrome, User2, Still cannot download the suspected folder, asks to enable third party cookies The Files That Were Causing Virus Alerts in Google Drive When Scanned on Windows 10's 'Anti-Virus Defender' Did Not Produce Alert List View: 1 ~\110809IMS_Student_CD_Setup.exe ~\files.html ~\gmat1 ~\gmat1.zip ~\gmat2 ~\gmat2.zip ~\gmat1\gmat1mx.exe ~\gmat1\gmat1vx.exe ~\gmat1\gmat2mx.exe ~\gmat1\gmat2vx.exe ~\gmat1\gmat3mx.exe ~\gmat1\gmat3vx.exe ~\gmat1\gmat4mx.exe ~\gmat1\gmat4vx.exe ~\gmat2\gmat5mx.exe ~\gmat2\gmat5vx.exe List View: 2 Volume in drive C is Windows Volume Serial Number is 8139-90C0 Directory of ~ 05/08/2021 10:00 PM <DIR> . 05/08/2021 10:00 PM <DIR> .. 05/08/2021 09:12 PM 42,742,301 110809IMS_Student_CD_Setup.exe 05/08/2021 10:00 PM 766 files.html 05/08/2021 10:00 PM 0 files2.html 05/08/2021 08:52 PM <DIR> gmat1 05/08/2021 08:49 PM 880,985 gmat1.zip 05/08/2021 08:52 PM <DIR> gmat2 05/08/2021 01:01 PM 210,131 gmat2.zip 5 File(s) 43,834,183 bytes Directory of ~\gmat1 05/08/2021 08:52 PM <DIR> . 05/08/2021 08:52 PM <DIR> .. 10/30/2000 05:41 PM 486,400 gmat1mx.exe 03/21/2001 01:29 AM 504,320 gmat1vx.exe 05/17/2001 09:21 PM 418,816 gmat2mx.exe 03/29/2001 07:54 PM 501,760 gmat2vx.exe 05/17/2001 09:18 PM 424,448 gmat3mx.exe 03/09/2001 11:17 AM 485,376 gmat3vx.exe 05/17/2001 09:27 PM 432,128 gmat4mx.exe 03/21/2001 01:35 AM 631,808 gmat4vx.exe 8 File(s) 3,885,056 bytes Directory of ~\gmat2 05/08/2021 08:52 PM <DIR> . 05/08/2021 08:52 PM <DIR> .. 05/17/2001 09:32 PM 425,984 gmat5mx.exe 03/09/2001 11:47 AM 486,912 gmat5vx.exe 2 File(s) 912,896 bytes Total Files Listed: 15 File(s) 48,632,135 bytes 8 Dir(s) 70,736,945,152 bytes free Tags: Technology,Cyber Security,Cloud,
Subscribe to:
Posts (Atom)