Following snippet is from Wikipedia (Dated: Jan 2021): Paracetamol, also known as acetaminophen, is a medication used to treat pain and fever. It is typically used for mild to moderate pain relief. Evidence is mixed for its use to relieve fever in children. It is often sold in combination with other medications, such as in many cold medications. Paracetamol is also used for severe pain, such as cancer pain and pain after surgery, in combination with opioid pain medication. It is typically used either by mouth or rectally, but is also available by injection into a vein. Effects last between two and four hours. Paracetamol was first made in 1877. It is the most commonly used medication for pain and fever in both the United States and Europe. It is on the World Health Organization's List of Essential Medicines. Paracetamol is available as a generic medication, with brand names including Tylenol and Panadol among others. In 2017, it was the 25th-most commonly prescribed medication in the United States, with more than 24 million prescriptions. Paracetamol is generally safe at recommended doses. The recommended maximum daily dose for an adult is three to four grams. Higher doses may lead to toxicity, including liver failure. Serious skin rashes may rarely occur. It appears to be safe during pregnancy and when breastfeeding. In those with liver disease, it may still be used, but in lower doses. It is classified as a mild analgesic. It does not have significant anti-inflammatory activity. Paracetamol's mechanism of action is not entirely clear. References: % 1 "Despite its long history and widespread use, paracetamol has no known endogenous binding sites and uncertainty persists regarding its mechanism and action." McKay GA, Walters MR (2013). "Non-Opioid Analgesics". Lecture Notes Clinical Pharmacology and Therapeutics (9th ed.). Hoboken: Wiley. ISBN 9781118344897. Archived from the original on 8 September 2017. Retrieved 7 September 2017. [ Link ] % 2 "In the U.S., approximately 79% of the general population consume APAP (or Acetaminophen) regularly (Link)." In addition to its antipyretic properties, APAP also produce analgesia. Several studies indicate that these two pharmacological outcomes occur through distinct mechanisms. Recently, a newly proposed mechanism of action for the analgesic properties of APAP has been described, which involves modulation of the endogenous cannabinoid system. This mechanism may provide an explanation for the “relaxation” or “calming” effect that has been reported in some patients that consume APAP. This effect is characterized by a peculiar sense of well-being, relaxation and tranquility. Note: Endocannabinoids are molecules that, like the plant cannabinoid THC, bind to and activate cannabinoid receptors. Endocannabinoids are produced naturally by cells in the human body (“endo” means “within,” as in within the body). The human body produces its own endogenous cannabinoids: natural equivalents of the compounds found in the cannabis plant, such as THC (tetrahydrocannabinol) and CBD (cannabidiol). Cannabinoid receptors, located throughout the body, are part of the endocannabinoid system, which is involved in a variety of physiological processes including appetite, pain-sensation, mood, and memory. Cannabinoid receptors are of a class of cell membrane receptors in the G protein-coupled receptor superfamily. Info: Ghanem CI, Pérez MJ, Manautou JE, Mottino AD (July 2016). "Acetaminophen from liver to brain: New insights into drug pharmacological action and toxicity". Pharmacological Research. 109: 119–31. doi:10.1016/j.phrs.2016.02.020. PMC 4912877. PMID 26921661. [ Link ] %3 "Acetaminophen, an analgesic (painkiller) that does not inhibit prostaglandin synthesis, lacks a systematic anti-inflammatory effect. In contrast to aspirin and other NSAIDs, acetaminophen does not affect systemic PgE2 concentrations. However, acetaminophen has some structural similarity to steroids and may have an anti-estrogenic effect, lowering follicular levels of LH, FSH, and estradiol." Viswanathan AN, Feskanich D, Schernhammer ES, Hankinson SE (2008). "Aspirin, NSAID, and Acetaminophen Use and the Risk of Endometrial Cancer". Cancer Research. 68 (7): 2507–2513. doi:10.1158/0008-5472.CAN-07-6257. PMC 2857531. PMID 18381460. [ Link ] Another Reference: HealthDirect: By Government of Australia How does paracetamol work? Paracetamol has been in general use for more than 50 years, but the way it works to reduce pain and fever is not fully understood. Paracetamol begins to ease pain and lower a high temperature about 30 minutes after a dose is taken. Its effects usually last for about 4 to 6 hours.
Pages
- Index of Lessons in Technology
- Index of Book Summaries
- Index of Book Lists And Downloads
- Index For Job Interviews Preparation
- Index of "Algorithms: Design and Analysis"
- Python Course (Index)
- Data Analytics Course (Index)
- Index of Machine Learning
- Postings Index
- Index of BITS WILP Exam Papers and Content
- Lessons in Investing
- Index of Math Lessons
- Downloads
- Index of Management Lessons
- Book Requests
- Index of English Lessons
- Index of Medicines
- Index of Quizzes (Educational)
Tuesday, January 12, 2021
Medical science does not know yet how paracetamol works
Journal (about English, Hindi and my mom)
Language is a means through which people communicate. It could be English, Hindi or Punjabi, for example. My first choice of using a language would be English as it is the language of business, law and academia in general. I also know Hindi and some amount of Punjabi since I’m in Chandigarh since 2018. My granddad knows five, viz., Hindi, English, Punjabi, Urdu and Sanskrit. My mom knows Hindi since it is the language that everyone uses in the Delhi and neighboring region. She also knows some amount of English, but it is not worth counting. It would be very useful if she or any other person could understand English because that is the language in which information is present on the internet. English is the language in which user manuals for any device or equipment is written. The information that you might receive via SMS from your bank or your telecom operator or electricity provider would be in English. But alas, knowing English does not mean that you also have gained communication skills, that you can express yourself and understand the other person as well. My friend Geeta Gulati was speaking to my mom and she asked her what kind of girl my mom would like as her daughter-in-law, and my mom said, “someone who is sanskaari and paarivaarik”. For non-Hindi speakers, I’d explain, “Sanskaari” means someone having moral values, etiquettes and manners. “Paarivaarik” means someone who values family and respects her or his family. Adding ‘family-oriented’ to the meaning of “Paarivaarik” would be like stretching it to an extreme. To refer to diet preferences, my mom said "shuddh shaakaahaari", which means vegetarian. My end note for this post would be that a person should keep learning a language or languages if there are more than one for self-improvement, but some flexibility should be allowed when we are not examining the grammar knowledge of a person.
Sunday, January 10, 2021
Why Amazon, Berkshire Hathaway, and JPMorgan's Haven failed
Why Jeff Bezos, Warren Buffett, and Jamie Dimon gave up on their venture to disrupt US healthcare So the CEOs of Amazon, Berkshire Hathaway, and JPMorgan Chase walked into largest and least efficient healthcare market in the world with a plan to disrupt it—and failed to do so. Haven, the nonprofit joint venture of the three companies, will end all operations this coming February, after three short years of operation. This development isn’t entirely unexpected, given that most of Haven’s top talent, including its CEO—doctor and high-profile healthcare researcher Atul Gawande, who led the initiative from its inception—had stepped down in the last several months. Haven’s goal was ambitious: to lower healthcare costs, first for the three companies’ hundreds of thousands of employees, and potentially for all Americans. “We’re able to focus on creating value for families, not shareholders, since we are free from profit-making incentives and constraints,” read the organization’s statement on its now-defunct website. The venture’s launch generated panic in the healthcare sector, with existing companies seeing it as a potential competitor. But Haven’s birth was cause for enthusiasm, too: It seemed such a formidable trio was destined to succeed despite the enormous challenges facing the US’ muddle of a medical system. It wasn’t, however. Haven’s goals, organization, and achievements over the last three years are still murky, so it’s hard to determine what exactly led to pulling the plug. But there are hints that point to the natural limits of the venture, and more concerningly, to those of the system it sought to disrupt. Mission: impossible Despite the secrecy around the venture, some of what might not have worked can be attributed to its management, as STAT News has reported. A few issues—such as a lack of visible progress, difficulties retaining talent, or the choice of a CEO who, while an expert in the field, had little experience running a company—hobbled the organization’s efforts. But other problems run deeper. These pertain to Haven’s goals, how they were set up, and whether they were ever remotely attainable. For one thing, Haven had a mission, but never quite a strategy, as Amitabh Chandra, the director of health policy research at the Harvard Kennedy School of Government tweeted. Its goal to “create simpler, high-quality healthcare at lower costs” (as the nonprofit’s site put it) was as vague as it was ambitious—a vision, rather than a business plan. Then there was the issue of the companies involved. Amazon, Berkshire Hathaway, and JPMorgan Chase employ a combined 1.2 million people spread around the country. This makes it an interesting test group for solutions to lower healthcare costs around the country. But that geographic diversity also created a very challenging group to serve, Brian Marcotte, the CEO of National Business Group on Health, told Christina Farr in a conversation on Second Opinion. Healthcare benefits are dependent on the location of the employee, and Haven couldn’t introduce the same programs to all local markets. Instead, it would have to set up plans wherever they had employees, without the critical mass to make it a worthwhile endeavor. Another problem, too, reported CNBC, was a divergence of interests between the three companies, each of which is expected to continue pursuing research in healthcare solutions for its own employees. Define disrupt Of the individual initiatives that may have accelerated the disbanding of Haven, Amazon Care is the most prominent. An initiative for Amazon employees living in the Seattle area, it seems to offer a product in line with what might have been devised by Haven. An additional benefit offered to employees who have signed up to get healthcare coverage from the company (through traditional insurance policies), Amazon Care allows patients to text with their clinicians, have telehealth visits, get medications delivered, and even see a nurse at home. It seeks to encourage people to make fewer expensive visits to the doctor’s office, by taking care of whatever can be managed without an in-person diagnosis or treatment. There aren’t yet data on whether Amazon Care is successfully reducing costs—for the employer and, less straightforwardly, for employees. But in any case, its goal is more limited than Haven’s: In the short- to medium-term, Amazon Care aims to save on existing policies, which would be a welcome change, but nowhere near a disruption of the system. Amazon Pharmacy, another healthcare initiative by Amazon, is much larger in scope. Launched in November, it’s, well, a large online pharmacy. It offers discounts (so far, only on drugs purchased without prescription), and free two-day shipping for Prime customers. But once again, it’s hard to see it as a disruption of anything—rather, it looks like Amazon entering a very lucrative business at a very opportune moment. No cure for the tapeworm “Healthcare is the tapeworm of the American economy,” Warren Buffett famously told CNBC in 2018, when presenting Haven. Indeed, the size of the market—fueled by costs exponentially higher than in any other country in the world—continues to expand relentlessly, and is projected to make up 20% of America’s GDP by 2028. But the results of this spending are paradoxical: Americans live shorter, less healthy lives than their peers in other countries, while suffering from an epidemic of bankruptcies related to medical issues (an estimated 66.5% of all bankruptcy filings are caused by medical expenses). Haven never explicitly said it would try to cure the tapeworm, but it’s telling how many hoped it just might be able to do so. The bandaids introduced by Obamacare in 2009 made it obvious that the US healthcare system is unsustainable, leaving a hunger for solutions: Perhaps employers could reform what the government wasn’t able to. According to a Haven spokesperson who spoke to CNBC, the company’s team did make progress in “piloting new ways to make primary care easier to access, insurance benefits simpler to understand and easier to use, and prescription drugs more affordable.” But all of these are small, marginal changes in a system whose cost is out of control. Even if clearer policies or transparent pricing reduced costs—which is not a given, as Chandra notes—the cumulative result would have a marginal benefit. “Haven is yet another cautionary tale to outsiders that hope to disrupt the industry that their ambition is likely unrealistic and that solving key industry problems proves to be far more difficult than most anticipate,” says Jeff Becker, an analyst at Forrester. By folding, Haven reduces hope in the possibility that private enterprise might fix US healthcare. And it leaves behind a loaded question: If some of the smartest, richest, most knowledgeable, well connected, and ambitious leaders in the room could not find a way to disrupt American healthcare, then who can? The message on Haven Healthcare's portal: In the past three years, Haven explored a wide range of healthcare solutions, as well as piloted new ways to make primary care easier to access, insurance benefits simpler to understand and easier to use, and prescription drugs more affordable. Moving forward, Amazon, Berkshire Hathaway, and JPMorgan Chase & Co. will leverage these insights and continue to collaborate informally to design programs tailored to address the specific needs of their own employee populations. Haven will end its independent operations at the end of February 2021.% Annalisa Merelli (Quartz) % https://qz.com/1952225/why-amazon-berkshire-hathaway-and-jpmorgans-haven-failed/
Friday, January 8, 2021
Nearly 40% components of Nifty50 changed in a decade ending in Dec 2020
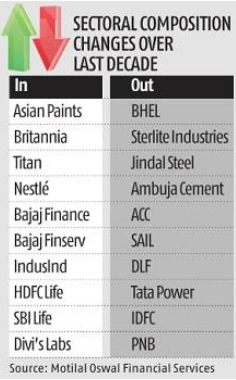
% Big names that are out of the index include BHEL, Sterlite Industries, Jindal Steel, Ambuja Cement, ACC, and SAIL. % The new entrants comprise Asian Paints, Britannia, Titan, Nestlé, BAF (Bajaj Finance), and Bajaj Finserv. % RIL, Infosys, ICICI Bank, and HDFC feature among the top five heavyweights even after a decade. % Twenty, or 40%, of components that were part of the Nifty50 in December 2010 are no longer part of the index today. % Sector weighting has also changed — those with high weighting a decade ago were oil and gas (14.7%), private banks (14.5%), and IT (14.3%). Sectors with high weighting in 2020 were private banks (24.7%), IT (16.3%) and oil and gas (12.5%). % Sectors which lost the most were metals (640 bps), and capital goods (610 bps); the biggest gainers were private banks (1,020 bps) and consumer (470 bps).https://www.business-standard.com/article/markets/nearly-40-components-of-nifty50-change-in-a-decade-shows-data-121010500039_1.html
Best Practices for Creating a Password
How does a password get hacked?
Cybercriminals have several password-hacking tactics at their disposal, but the easiest one is simply to buy your passwords off the dark web. There’s big money in the buying and selling of login credentials and passwords on the blackmarket, and if you’ve been using the same password for many years, chances are it’s been compromised. But if you’ve been wise enough to keep your passwords off the aggregated blackmarket lists, cybercriminals have to crack them. And if that’s the case, they’re bound to use one of the methods below. These attacks can be aimed at your actual accounts or possibly at a leaked database of hashed passwords. Brute force attack This attack tries to guess every combination in the book until it hits on yours. The attacker automates software to try as many combinations as possible in as quick a time as possible, and there has been some unfortunate headway in the evolution of that tech. In 2012, an industrious hacker unveiled a 25-GPU cluster he had programmed to crack any 8-character Windows password containing uppercase and lowercase letters, numbers, and symbols in less than six hours. It has the ability to try 350 billion guesses per second. Generally, anything under 12 characters is vulnerable to being cracked. If nothing else, we learn from brute force attacks that password length is very important. The longer, the better. Dictionary attack This attack is exactly what it sounds like — the hacker is essentially attacking you with a dictionary. Whereas a brute force attack tries every combination of symbols, numbers, and letters, a dictionary attack tries a prearranged list of words such as you’d find in a dictionary. If your password is indeed a regular word, you’ll only survive a dictionary attack if your word is wildy uncommon or if you use multiple word phrases, like LaundryZebraTowelBlue. These multiple word phrase passwords outsmart a dictionary attack, which reduces the possible number of variations to the number of words we might use to the exponential power of the number of words we’re using, as explained in the “How to Choose a Password” video by Computerphile. Phishing That most loathsome of tactics — phishing — is when cybercriminals try to trick, intimidate, or pressure you through social engineering into unwittingly doing what they want. A phishing email may tell you (falsely) that there’s something wrong with your credit card account. It will direct you to click a link, which takes you to a phony website built to resemble your credit card company. The scammers stand by with bated breath, hoping the ruse is working and that you’ll now enter your password. Once you do, they have it. Phishing scams can try to ensnare you through phone calls too. Be leery of any robocall you get claiming to be about your credit card account. Notice the recorded greeting doesn’t specify which credit card it’s calling about. It’s a sort of test to see if you hang up right away or if they’ve got you “hooked.” If you stay on the line, you will be connected to a real person who will do what they can to wheedle as much sensitive data out of you as possible, including your passwords.The anatomy of a strong password
Don’t be silly Stay away from the obvious. Never use sequential numbers or letters, and for the love of all things cyber, do not use “password” as your password. Come up with unique passwords that do not include any personal info such as your name or date of birth. If you’re being specifically targeted for a password hack, the hacker will put everything they know about you in their guess attempts. Can it be brute force attacked? Keeping in mind the nature of a brute force attack, you can take specific steps to keep the brutes at bay: - Make it long. This is the most critical factor. Choose nothing shorter than 15 characters, more if possible. - Use a mix of characters. The more you mix up letters (upper-case and lower-case), numbers, and symbols, the more potent your password is, and the harder it is for a brute force attack to crack it. - Avoid common substitutions. Password crackers are hip to the usual substitutions. Whether you use DOORBELL or D00R8377, the brute force attacker will crack it with equal ease. These days, random character placement is much more effective than common leetspeak* substitutions. (*leetspeak definition: an informal language or code used on the Internet, in which standard letters are often replaced by numerals or special characters.) - Don’t use memorable keyboard paths. Much like the advice above not to use sequential letters and numbers, do not use sequential keyboard paths either (like qwerty). These are among the first to be guessed. Can it be dictionary attacked? The key to staving off this type of attack is to ensure the password is not just a single word. Multiple words will confuse this tactic — remember, these attacks reduce the possible number of guesses to the number of words we might use to the exponential power of the number of words we are using, as explained in the popular XKCD post on this topic. How about this: Through 20 years of effort, we've successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.The best password methods (and great password examples)
The revised passphrase method This is the multiple word phrase method with a twist — choose bizarre and uncommon words. Use proper nouns, the names of local businesses, historical figures, any words you know in another language, etc. A hacker might guess Quagmire, but he or she would find it ridiculously challenging to try to guess a good password example like this: QuagmireHancockMerciDeNada While the words should be uncommon, try to compose a phrase that gives you a mental image. This will help you remember. To crank it up another notch in complexity, you can add random characters in the middle of your words or between the words. Just avoid underscores between words and any common leetspeak* substitutions. (*leetspeak: an informal language or code used on the Internet, in which standard letters are often replaced by numerals or special characters.) The sentence method This method is also described as the "Bruce Schneier Method." The idea is to think of a random sentence and transform it into a password using a rule. For example, taking the first two letters of every word in “The Old Duke is my favorite pub in South London” would give you: ThOlDuismyfapuinSoLo To anyone else, it’s gobbledygook, but to you it makes perfect sense. Make sure the sentence you choose is as personal and unguessable as possible.Recommended ways to improve your password portfolio
All of the above methods help to strengthen your passwords but aren’t very workable, given that the average person uses dozens of them. Let’s review a few ways we recommend: use new complex passwords and a password manager, install an authenticator app on your smartphone, and purchase new hardware. Each of these can help with better and more secure authentications. Use a password manager and a random password generator A password manager keeps track of all of your passwords and does all the remembering for you, except for one thing — the master password which grants you access to your password manager. For that big kahuna, we encourage you to use every tip and trick listed above. The programs also come with generators, so you can create super-complicated, extra-long passwords that are infinitely more difficult to crack than any passwords a human might come up with. PC Magazine has a series of recommendations of password managers here. Be careful who you trust Security-conscious websites will hash its users’ passwords so that even if the data gets out, the actual passwords are encrypted. But other websites don’t bother with that step. Before starting up accounts, creating passwords, and entrusting a website with sensitive info, take a moment to assess the site. Does it have https in the address bar, ensuring a secure connection? Do you get the sense it is up on the newest security standards of the day? If not, think twice about sharing any personal data with it. Use multi-factor authentication Multi-factor authentication (MFA) adds an extra layer of protection (which becomes your first layer of protection should your account details ever get leaked). These have become the new industry standard for effective security. In our blog post here, we explain how they are used and how you can add MFA to common social accounts such as Twitter and Facebook. They require something in addition to a password, such as biometrics (fingerprint, eye scan, etc.), or a physical token. This way, as simple or complex as your password is, it’s only half of the puzzle. Note: given the 2018 Reddit hack caused by SMS-intercepts, we do not recommend using SMS as your second factor of authentication. This is a well-trod path by many hackers in the past few years.Notes
1. Password storage in Firefox If you have not enabled and assigned a “master password” to manage your passwords in Firefox, anyone with physical access to your computer and user account can view the stored passwords in plain text, simply by clicking “Options,” and then “Show Passwords.” To protect your passwords from local prying eyes, drop a check mark into the box next to “Use Master Password” at the main Options page, and choose a strong password that only you can remember. You will then be prompted to enter the master password once per session when visiting a site that uses one of your stored passwords. 2. Avoid Periodic Changes of Personal Passwords A widespread password security practice over the years has been to force users to change passwords periodically—every 90 days, or 180 days, etc. However, more recent guidance from NIST advises not to use a mandatory policy of password changes for personal passwords (note that this updated guidance does not apply to privileged credentials) One reason is that users tend to just repeat passwords they had used before. You can implement strategies to prevent password re-use, but users will still find creative ways around it. The other consequence of frequent password changes is that users are more likely to write the passwords down to keep track of them. Thus, a best practice from NIST is to ask employees for password change only in case of potential threat or compromise. 3. These 7 tips will help make your digital life more secure 3.1. Never reveal your passwords to others. You probably wouldn’t give your ATM card and PIN to a stranger and then walk away. So, why would you give away your username and password? Your login credentials protect information as valuable as the money in your bank account. Nobody needs to know them but you—not even the IT department. If someone is asking for your password, it’s a scam. 3.2. Use different passwords for different accounts. That way, if one account is compromised, at least the others won’t be at risk. 3.3. Use multi-factor authentication (MFA). Even the best passwords have limits. Multi-Factor Authentication adds another layer of protection in addition to your username and password. Generally, the additional factor is a token or a mobile phone app that you would use to confirm that you really are trying to log in. Learn more about MFA and how to turn it on for many popular websites at https://twofactorauth.org/. 3.4. Length trumps complexity. The longer a password is, the better. Use at least 16 characters whenever possible. 3.5. Make passwords that are hard to guess but easy to remember. - To make passwords easier to remember, use sentences or phrases. For example, “breadandbutteryum”. Some systems will even let you use spaces: “bread and butter yum”. - Avoid single words, or a word preceded or followed by a single number (e.g. Password1). Hackers will use dictionaries of words and commonly used passwords to guess your password. - Don’t use information in your password that others might know about you or that’s in your social media (e.g. birthdays, children’s or pet’s names, car model, etc.). If your friends can find it, so will hackers. 3.6. Complexity still counts. To increase complexity, include upper and lower case letters, numbers, and special characters. A password should use at least 3 of these choices. To make the previous example more secure: “Bread & butter YUM!” 3.7. Use a password manager. Password management tools, or password vaults, are a great way to organize your passwords. They store your passwords securely, and many provide a way to back-up your passwords and synchronize them across multiple systems. Though the University does not recommend any one solution, here are some examples of free password managers*: LastPass: https://lastpass.com/ KeePass: https://keepass.info/ Keeper: https://keepersecurity.com/ Password Safe: https://pwsafe.org/ Dashlane: https://dashlane.com/ 4. Password mistakes you should avoid - Avoid easily guessed passwords. The problem basically starts with password recycling, which is a risky practice. Substituting lower case for upper case or vice versa is also password recycling. - Don’t add personal information in your passwords. If your password includes your name, surname, birthday, address or phone number, then you must consider changing it. - Don’t use the same password across several accounts. This may be the easiest way to remember your passwords. Unfortunately, it is also the fastest way to trouble. Did you know that in 2016, Mark Zuckerberg’s Linkedin, Twitter and Pinterest accounts were hacked, as he was using the same password for multiple social media platforms? 5. 5 Password security best practices 5.1. Make sure your password is complex So is a long password the way to go? Possibly, yes. Short length passwords are easy to hack. For added security, try to create lengthier passwords. Using upper and lowercase alphanumerical characters is also one of the best practices to boost password security. To increase the complexity of your password, you can add spaces, punctuation, or misspellings to your password. Implementing all these will make your password less predictable. Don’t forget that the length of your password is a significantly important attribute. 5.2. Use a word that can’t be found in a dictionary There are multiple ways that criminals use to find passwords. A brute force attack is one of them. These attacks are the random trial-and-error sessions or repeated successive attempts of guessing password combinations. Hackers simply let the bot do the job – executing a high number of attempts per minute until they find a password. If you must use a dictionary word, try these: either combine your password with a number or add punctuation at the beginning or at the end of the word. Simply put, get creative and formulate really unique combinations. 5.3. When possible, use brackets Feel free to use curly { }, round ( ), square [ ] or even angle < > brackets. They are rarely used by people. So, this makes them a great way of boosting password security. The more you mix up letters with brackets or symbols, the harder it is for a hacker to compromise it. 5.4. Use misspelling words Bad spelling or password typos can actually make a huge difference in your overall password security. Hackers usually are searching for passwords using correct grammar and spellings in their attacks. The potential benefit of this method is the fact that it enables you to create more complicated passwords. 5.5. Change your passwords as required. Stay one step ahead of hackers by changing your passwords. But there is a problem that comes with changing your passwords regularly. We don’t actually mean changing a password every month. You may naturally wonder what is the best time to change the password. We would say it is when a website you have an account for is hacked. Additionally, if you have shared your password with somebody else, it is time to change your password. Did you know that 57% of people who have experienced a phishing attack have not changed their password management techniques? 6. Add Extra Security to your C-Suite Not everyone in your company handles sensitive information. It’s important that you use the right security measures for the position. C-suite executive positions require more password management than your intern. Naturally, executive staff handle more sensitive information and therefore need a more secure password. Multi-factor authentication can be expensive—especially if you’re using biometrics. Spend your money wisely by applying biometrics to upper management and other mission critical roles while encouraging the rest of your staff to use password management best practices. 7. It’s no secret that malicious cyber activity costs businesses and the economy dearly. In fact, data hacks and breaches cost the U.S. economy between $57 billion and $109 billion in 2016. For small business, the cost and damage of a data hack can be irreversible. A staggering 81% of company data breaches are due to poor passwords. The good news is that by taking some simple but effective precautions in relation to passwords, businesses can help protect themselves from the havoc and damage data breaches can cause. 8. 5 Common Password-Cracking Techniques Used by Hackers 8.1. Dictionary attacks These are attacks on passwords that resemble words from the dictionary. They can also be the derivatives of commonly used words where letters are replaced with numeric or alphanumeric characters. 8.2. Brute force attack These are attacks on passwords that have no meaning, that is, do not resemble any dictionary word. Examples include all the probable combinations from aaa1 to zzz10. The hacker will keep trying as many passwords and paraphrases as possible hoping to get lucky in the guessing game. 8.3. Cracking security questions As one of the commonly used techniques of two-factor authentication as a lot of people prefer using security questions – because they are easy to remember. But then, they are also easy for hackers to crack the answers as they are mostly available on social media profiles. All they need to do is a little bit of digging. 8.4. Social engineering attack Here hackers play with users’ psychology and trick them into disclosing their passwords. A common example of a social engineering attack is phishing where hackers come up with irresistible offers and manipulate users to respond to malicious links and steal their credentials. 8.5. Spidering A lot of passwords in corporate businesses are made up of words around the business itself. Savvy hackers study corporate literature and build a list of custom words to launch a brute force attack against those passwords.References: % https://blog.avast.com/strong-password-ideas % https://krebsonsecurity.com/password-dos-and-donts/ % https://www.beyondtrust.com/blog/entry/top-15-password-management-best-practices % https://www.it.ucsb.edu/secure-compute-research-environment-user-guide/password-best-practices % https://www.swisscyberforum.com/is-your-password-secure/ % https://www.pluralsight.com/blog/security-professional/modern-password-guidelines % https://swiftsystems.com/guides-tips/10-best-practices-for-password-management/ % https://www.godaddy.com/garage/10-best-practices-for-creating-and-securing-stronger-passwords/ % https://smallbiztrends.com/2019/01/password-best-practices.html % https://www.business2community.com/cybersecurity/password-security-best-practices-in-2020-02282074
Saturday, January 2, 2021
Don't Endure. Recharge (Lesson in Emotional Intelligence)
As constant travelers and parents of a two-year-old, we sometimes fantasize about how much work we could do if we could just get on a plane, undistracted by phones, friends, or Finding Nemo. And so in advance of a trip, we race to get all our groundwork done: packing, going through TSA, doing a last-minute work call, calling each other, boarding. But then when we try to have that amazing in-fl ight work session, we fi nd that we get nothing done. Even worse, after refreshing our email or reading the same studies over and over, we are too exhausted when we land to soldier on with the emails that have inevitably still piled up. Why can’t we be tougher—more resilient and determined in our work—so we can accomplish all of the goals we set for ourselves? Through our current research, we have come to realize that the problem comes from a cultural misunderstanding of what it means to be resilient, and the resulting impact of overworking. As a society, we often associate “resilience” and “grit” with a militaristic, “tough” approach to our work. We imagine a Marine slogging through the mud, a boxer going one more round, or a football player picking himself up off the turf for one more play. We believe that the longer we tough it out, the tougher we are, and therefore the more successful we will be. However, this entire conception is scientifi cally inaccurate. In fact what’s holding back our ability to be resilient and successful is the lack of any kind of recovery period. Resilience is defined as the ability to quickly bounce back from stressful situations—no matter what problems are thrown at us, we continually get back up, ready for the next one. But even for the most resilient person, getting ready doesn’t happen instantly. It is a process—and an important one. Research has found that there is a direct correlation between lack of recovery and increased incidence of health and safety problems. And lack of recovery—whether it disrupts our sleep with thoughts of work or keeps us in continuous cognitive arousal as we obsessively watch our phones—is costing our companies $62 billion a year (that’s billion, not million) in lost productivity. [1] Misconceptions about resilience as nonstop activity and energy are often bred into us from an early age. For instance, parents might praise the resilience of their high school student who stays up until 3 a.m. to finish a science fair project. But when that exhausted student drives to school, his impaired driving poses risks for himself and others; at school, he doesn’t have the cognitive resources to do well on his English test and has lower self-control with his friends; and at home, he is moody with his parents. The bad habits we learn when we’re young only magnify when we hit the workforce. In a study released last month, researchers from Norway found that 7.8% of Norwegians have become workaholics, where workaholism is defi ned as “being overly concerned about work, driven by an uncontrollable work motivation, and investing so much time and effort to work that it impairs other important life areas.” [2] And in fact that drive can backfire in the very area for which we’re sacrifi cing ourselves: In her excellent book 'The Sleep Revolution: Transforming Your Life, One Night at a Time', Arianna Huffington wrote, “We sacrifi ce sleep in the name of productivity, but ironically our loss of sleep, despite the extra hours we spend at work, adds up to 11 days of lost productivity per year per worker, or about $2,280.” [3] The key to resilience is not working really hard all the time. It is actually found in the time that we stop working and recover. Ideally, we need to create cycles for ourselves in which we work hard, then stop and recover, and then work again. This conclusion is based on biology. Homeostasis, a fundamental biological concept, is the ability of the body to continuously restore and sustain its own well-being. When the body is out of alignment and therefore in a state of stress or exhaustion from overworking, we waste a vast amount of mental and physical resources trying to return to balance before we can move forward. As Jim Loehr and Tony Schwartz have written in The Power of Full Engagement, the more time you spend in the performance zone, the more time you need in the recovery zone; otherwise you risk burnout. And if, instead of taking a break, you muster your resources to continue to “try hard,” you need to burn ever more energy in order to overcome your currently low arousal level, which only exacerbates your exhaustion. It’s a vicious downward spiral. But the more imbalanced we become due to overworking, the more value there is in activities that allow us to return to a state of balance. So what are those activities that allow us to return to homeostasis and thereby increase our resilience? Most people assume that if you stop doing a task like answering emails or writing a paper, that your brain will naturally recover, so that when you start again later in the day or the next morning, you’ll have your energy back. But stopping work doesn’t mean you’re actually recovering: If after work you lie around on the couch and check your phone and get riled up by political commentary, or get stressed thinking about decisions about how to renovate your home, your brain has not received a break from high mental arousal states. And surely everyone reading this has occasionally lain in bed for hours, unable to fall asleep because their brain is thinking about work, even if they don’t have a device in hand. If you’re in bed for eight hours, you may have rested, but you can still feel exhausted the next day. That’s because rest and recovery are not the same thing. If you’re trying to build resilience at work, you need adequate internal and external recovery periods. As researchers F. R. H. Zijlstra, M. Cropley, and L. W. Rydstedt wrote in a 2014 paper: “Internal recovery refers to the shorter periods of relaxation that take place within the frames of the workday or the work setting in the form of short scheduled or unscheduled breaks, by shifting attention or changing to other work tasks when the mental or physical resources required for the initial task are temporarily depleted or exhausted. External recovery refers to actions that take place outside of work—e.g., in the free time between the workdays, and during weekends, holidays or vacations.” [4] There are four main researched ways to increase your resilience. First, start by deliberately opening a space for recovery to happen. We’ve worked with several companies that tout the benefi ts of investing in employee wellbeing, but fail to create tangible results because they don’t carve out time for their workers to devote part of their workday to those rejuvenating activities. Adding more activities to an already full plate of work increases the stress load. Second, it is crucial that you take all of your paid time off. As we described in a previous HBR article entitled “The Data-Driven Case for Vacation,” taking your days off not only gives you recovery periods to recharge, but in fact signifi cantly raises your productivity and the likelihood of promotion. Third, while it might sound counterintuitive, it is possible to use technology to limit tech use while building internal recovery periods into your daily routine. The average person turns on their phone 150 times every day. [5] If every distraction took only 1 minute (which would be seriously optimistic), that would account for 2.5 hours of every day. In her upcoming book The Future of Happiness, based on her work at Yale Business School, Amy Blankson suggests downloading the Instant or Moment apps to see how many times you turn on your phone each day; using the app reminds you to make a choice in those moments when you grab your phone—and choose to stay away. You can also use apps like Offtime or Unplugged to create tech-free zones by strategically scheduling automatic airplane modes. In addition, you can take a cognitive break every 90 minutes to recharge your batteries. Try to not have lunch at your desk, but instead spend time outside or with your friends—not talking about work. Fourth, now that you have carved out time for rejuvenation, it’s time to engage in an activity or two that make you feel happy and replenished. Take the pressure off and just do something for the fun of it! Go on a walk or run, call and old friend, meditate by watching your breath go in and out for fi ve minutes, try a new recipe, or do something nice for someone else. Choose to do something that makes you feel alive, gives you a mental break from work, and keeps you fully engaged the whole time. Not only does spending your time this way help you come back stronger, oftentimes these activities are more memorable in the long run. As for us, we’ve started using our plane time as a work-free zone, and thus as time to dip into the recovery phase. The results have been fantastic. We are usually tired already by the time we get on a plane, and the cramped space and spotty internet connection make work more challenging. Now, instead of swimming upstream, we relax, meditate, sleep, watch movies, journal, or listen to entertaining podcasts. And when we get off the plane, instead of being depleted, we feel rejuvenated and ready to return to the performance zone. About the author Shawn Achor is New York Times best-selling author of The Happiness Advantage and Before Happiness. His TED talk is one of the most popular, with over 14 million views. He has lectured or researched at over a third of the Fortune 100 and in 50 countries, as well as for the NFL, NASA, and the White House. He is leading a series of courses on “21 Days to Inspire Positive Change” with the Oprah Winfrey Network. Michelle Gielan, a national CBS News anchor turned UPenn positive psychology researcher, is the best-selling author of Broadcasting Happiness. She is partnered with Arianna Huffington to research how a solution-focused mindset fuels success, and shares her research at organizations including Google, American Express, and Boston Children’s Hospital. Michelle is the host of the Inspire Happiness program on PBS. NOTES 1. J. K. Sluiter, “The Influence of Work Characteristics on the Need for Recovery and Experienced Health: A Study on Coach Drivers,” Ergonomics 42, no. 4 (1999): 573–583; and American Academy of Sleep Medicine, “Insomnia Costing U.S. Workforce $63.2 Billion a Year in Lost Productivity,” ScienceDaily, September 2, 2011. 2. C. S. Andreassen et al., “The Relationships Between Workaholism and Symptoms of Psychiatric Disorders: A Large-Scale Cross-Sectional Study,” PLoS One 11, no. 5 (2016): e0152978. 3. Ronald C. Kessler et al., “Insomnia and the Performance of US Workers: Results from the America Insomnia Survey,” Sleep 34, no. 9 (2011): 1161–1171. 4. F. R. H. Zijlstra et al., “From Recovery to Regulation: An Attempt to Reconceptualize ‘Recovery from Work’” (special issue paper) (Hoboken, NJ: John Wiley & Sons, 2014), 244. 5. J. Stern, “Cellphone Users Check Phones 150x/Day and Other Internet Fun Facts,” Good Morning America, May 29, 2013. Adapted from content posted on hbr.org on June 24, 2016, as “Resilience Is About How You Recharge, Not How You Endure” (product #H02Z3O)
Friday, January 1, 2021
Negotiation between Ecuador and Peru to end the border conflict in 1998
A Personal Account by Jamil Mahuad, Former President of Ecuador A fifty-year boundary dispute between Ecuador and Peru ended through the successful negotiation between Jamil Mahuad, president of Ecuador (1998–2000), and Alberto Fujimori, president of Peru (1990–2000). President Mahuad has taken two negotiation courses at Harvard University—one several years ago with Roger and a seminar more recently with Roger and Dan that explicitly articulated the core concerns framework. During our seminar, President Mahuad realized the extent to which he intuitively had used the core concerns to help resolve the Peru–Ecuador border dispute. We invited him to contribute this chapter to share with readers his creative use of those concerns. I took office as president of Ecuador on August 10, 1998, after serving six years as mayor of Quito, my country’s capital. The main motivation for entering the presidential race was to alleviate poverty and to reduce inequality in my Nevada-sized Andean country of 12 million people. My political strategy was to replicate at a national level the successful formula that I had used while mayor of Quito’s 1.2 million people. My formula was: “Promise attainable projects, deliver on my promises, and stay close to the people.” While I was mayor, Fortune magazine considered Quito one of the ten Latin American cities that greatly improved the quality of life of its citizens. As I took office, however, the Ecuadorian economy was spiraling into— arguably—its worst economic crisis of the twentieth century. Simultaneously, political, military, and diplomatic experts foresaw an imminent and perhaps unavoidable new armed conflict with Peru. THE PERFECT STORM If you have read The Perfect Storm or have seen the movie based on the book, you’ll have the right mind-set to understand Ecuador’s situation in 1998 and 1999. The film depicts how, in October 1991, the unique combination of three immense meteorological events produced a storm stronger than any in recorded history. A hurricane from the Caribbean and two fronts from Canada and the Great Lakes converged and fed each other in the Atlantic. The storm trapped a small fishing boat from Gloucester, Massachusetts, and doomed its entire crew. Here’s where the analogy comes through. In 1998–1999, Ecuador was suffering from the once-in-a-century combined effects of: - The coastal destruction left by El Niño floods (the largest in five hundred years) - Record low-level oil prices (oil then accounted for around half of the Ecuadorian exports and the government’s revenue) - The Asian economic crisis (the first global economic crisis) These factors came on top of a fiscal deficit of 7 percent of the GDP; the final puffings of a crashing financial system; and a physically destroyed and paralyzed private sector. The inflation rate was 48 percent and the debt to GDP ratio was more than 70 percent—both the highest in Latin America. Consequently, international creditors—mistrusting Ecuador’s capacity for servicing its debt—were demanding full repayment of loans at maturity and closing their lines of credit. This economic meltdown demanded immediate attention. My top shortterm priorities were to reduce the fiscal deficit and consequently decrease the inflation rate; to reconstruct the Pacific coastal area of the country recently devastated by the flood; and to restore the country’s credit worthiness through a program with the International Monetary Fund that would get new financing for my social programs, mainly health and education. Nevertheless, an unexpected twist in the international front forced me to change priorities and work first to avoid a war with Peru. I considered this situation to be my first and most important responsibility morally, ethically, and economically. An international war would have escalated our already critical situation into a desperate one. How could Ecuador face an international war with the economy already in shambles? I needed a definitive peace accord with Peru in order to reduce the military budget, to dedicate our scarce resources to invest in social infrastructure, and to focus our attention and energies on growth and development. THE CURRENT SITUATION The long, tough, disappointing history of armed conflict with Peru represented for Ecuadorians a painful wound. Ecuadorians felt abused, stripped of their legitimate territories by the force of a powerful neighbor supported by the international community. Here was the scenario the moment I took office: - “The oldest armed conflict in the Western Hemisphere.” The United States State Department called the Ecuador–Peru border dispute the “oldest armed conflict in the Western Hemisphere.” Its roots can be traced back at least to the discovery of the Amazon River in 1542 by the Spanish conquistador Francisco de Orellana or, even before that, to the 1532 precolonial Indian war for the control of the Inca Empire between the Quiteño Atahualpa (now Ecuador) and the Cusqueño Huascar (now Peru). - The largest land dispute in Latin America. The territory historically claimed by both Ecuador and Peru was bigger than France. It constituted the largest disputed territory in Latin America and one of the largest in the world. - Numerous attempts to resolve the conflict had failed. Since the early nineteenth century attempts to reach a solution consistently failed. The countries had tried war, direct conversation, and amicable intervention by third parties, mediation, and first-class arbiters including the King of Spain and President Franklin Roosevelt. None yielded a positive result. The last period of this conflict started in 1942. After an international war between Ecuador and Peru in mid-1941 and following the Japanese attack on Pearl Harbor in December 1941, the United States pressed Ecuador and Peru to end definitively their land dispute. In 1942 in Rio de Janeiro, the two countries signed a treaty called the Protocol of Peace, Friendship and Limits. Known in short as the Rio Protocol, this treaty was guaranteed by Argentina, Brazil, Chile, and the United States. The Rio Protocol established that part of the boundary between Ecuador and Peru would be a watershed (a ridge of high ground) between the Santiago and Zamora rivers. It turned out, however, that between these two rivers there was not a single watershed, but a third river, the Cenepa. As a result, out of a 1500 kilometer-long block of land marked frontier, approximately 78 kilometers remained an “open wound.” Armed conflict erupted in 1981 and again in 1995, but did not settle the issue. On the contrary, more bitterness and mutual mistrust developed. This zone was epitomized by the outpost of Tiwintza, a small area of land where soldiers from both countries had been killed and buried. Tiwintza became a heroic symbol to each country. The post-1995 negotiation process had advanced important agreements regarding future joint projects, mutual security, trust, commerce, and navigational rights over some tributaries of the Amazon. Nonetheless, all this progress was contingent on a final agreement over Tiwintza. As an almost final effort to overcome entrenched positions, Ecuador and Peru asked a special commission for a nonmandatory but morally important opinion (a Parecer) on the issue. The special commission was known as a Juridical–Technical International Commission and included representatives of Argentina, Brazil, and the United States. The opinion of the commission was released a few weeks before I was elected president. It expressed the view that Tiwintza was part of the sovereign territory of Peru. That opinion, contrary to the situation on the ground where Ecuadorian troops had been for decades, stirred up escalating hostility between the two countries. By the time I took office, the troops from Ecuador and Peru had occupied the previously agreed upon demilitarized zone. They faced one another so closely that, in some places, they could shake hands and say Buenos días before raising their rifles. The Ecuadorian military command briefed me that a Peruvian invasion starting a few hours after my inauguration was a likely scenario. Peru would most likely provoke not a localized but a generalized armed conflict. The magnitude of this risk was perceived only by the most informed echelon of society. The rest of the country was immersed in their struggle to survive the economic difficulties and was distracted temporarily by the new president’s inauguration. THE CHALLENGE: AGAINST ALL ODDS Upon stepping into office, pursuing peace with Peru would require: - Belief. There would have to be the popular belief that the war could be resolved. Myths are almost impossible to debunk; the intractability of the problem with Peru had deep roots in Ecuadorians’ flesh and souls. - Civic participation. Making peace between Ecuador and Peru would have to be a “people’s project,” not a government issue. There would need to be a boost in participation of the people represented by any legitimate organization or group. - Trust. Cooperation and mutual trust would need to be elicited from all sectors in this fragmented country. - Political support. A formula for peace would need to be created. It would have to be acceptable for both countries and for many different sectors in each country. - Economic stability. There would need to be ways to bring economic stability to a country on the verge of war. In such a moment of distress, how could the government go about dictating badly needed, but unpopular, economic adjustments that would compromise the national unity and governability of Ecuador? - A clear, coherent, comprehensive action plan. The resulting plan would need to be not only military but also economic, political, and international in scope. PREPARING FOR PEACE Since the purpose of this chapter is showing the core concerns in action, I’ll focus my attention on the negotiation strategy of the border conflict and some interactions with my colleague, President Alberto Fujimori of Peru, while ignoring the complications of the economic situation in Ecuador. I needed a talented governmental cabinet to carry out peace efforts. Dr Jose Ayala, allegedly the most respected Ecuadorian diplomat, had been minister of foreign affairs and had conducted peace negotiations. I asked him to remain in his role. General Jose Gallardo had been minister of defense during the most recent armed conflict in 1995; that conflict had ended with an Ecuadorian military victory. I appointed General Gallardo to be minister of defense. In short, I appointed the chancellor of peace and the general of war as members of my cabinet. This was done to send a clear signal: Although Ecuador was openly inclined to a peaceful solution, we were ready to defend ourselves fiercely if necessary. Chancellor Ayala informed me of the general perception that nearly every contentious issue had been agreed upon by the two diplomatic delegations. The remaining point, the territorial dispute of the zone symbolized by Tiwintza, was something that only the presidents themselves could decide. It required a final stage of diplomacy at the highest level —“Presidential Diplomacy” as the press labeled it. I phoned Professor Roger Fisher at his Harvard Law School office and invited him to come to Quito and join the Ecuadorian government team to analyze the current situation, brainstorm possible approaches, and prepare a negotiation strategy. When Roger arrived in Quito, we worked on various fronts simultaneously. We carefully reviewed with the ministers of defense and foreign affairs the up-to-date military and diplomatic facts. To get everybody on the same page, Roger offered, for the benefit of some cabinet and staff members connected with the negotiation, a half-day presentation of his classic Seven Elements of Negotiation and some useful techniques for their application. Due to the current tensions, a personal meeting of the two presidents was most unlikely to occur. However, in preparation for an eventual encounter with President Fujimori, Roger and I examined ways to start a personal working relationship. The first two or three days in any new job can be hectic. A presidential office is no exception. Our meetings were frequently interrupted by urgent events. We had some of our sessions at odd times and places. I remember slipping Roger into my office between two scheduled appointments and meeting him in the dining room of my residence in the palace after eleven at night. KEY ELEMENTS IN BUILDING EMOTIONAL RAPPORT In a negotiation process, the relationship among the negotiators is as important as the substance of the negotiation. My first strategic decision was to build upon the existing working relationship already established between the two national negotiation teams. My nondelegable, crucially important mission was to build personal rapport with President Fujimori, a man I had not met. It was a challenge to figure out how I would do that. In my third day in office, I received an unexpected call from President Cardoso of Brazil. He invited me to a personal meeting with President Fujimori in Asuncion del Paraguay, where all three of us were scheduled to be thirty-six hours later for the inauguration of President Cubas. Two facts were clear to me. I badly needed that first encounter. And I was not yet ready to tackle the substance of the problem. How could I communicate the seriousness of my intentions to President Fujimori without giving him the impression that I was just buying time and procrastinating? Appreciation: Show Your Understanding of His Merits and Difficulties Our team agreed to make it clear to President Fujimori that I appreciated his years of involvement in the boundary problem and the knowledge he must have derived from that experience. That assessment of President Fujimori’s situation would have been plainly true for any dispassionate observer. I expected that such initial recognition would help us find an emotional common ground to serve as a basis for future conversations. My preparation with Roger started like this: ROGER: What is the purpose of your first meeting with President Fujimori? JAMIL: I see two purposes. I want to get to know him and his vision about the current situation. And I want to get his commitment that we are going to exhaust dialogue before stepping into war. For these purposes, I would like to listen first and ask him questions. ROGER: Great purposes. But if you go after him with a lot of questions, he may feel as if the FBI is interrogating him. He’s likely to clam up. An easier and perhaps wiser approach would be to have President Fujimori come to feel that he knows you. Be open. Start by laying some of your cards on the table. That was precisely what I did. Using stories, historical examples, and anecdotes, I explained to President Fujimori how I understood the difficult situation he was facing. I asked for his reciprocal understanding of the extremely complex scenario I was acting on. He responded well, although cautiously. In a soft, tranquil voice, he stated, “My three goals when I started my presidency were to eliminate hyperinflation, to dismember the Shining Path guerrillas, and to finish the border issue with Ecuador. I have accomplished the first two already. The third one must be concluded as well.” That gave me the opportunity to express frankly my admiration for his work on both of the first two issues, which was universally applauded, while adopting a wait-and-see attitude about the third. Affiliation: Find Some Common Ground A major task was to change the widespread perception of the bad relationship between the two countries. This task was faced by President Fujimori and myself, as well as by our staff and officials, the media, and the public at large. For years, each country had regarded the other as an enemy. President Fujimori and I agreed that a goal should be to have the public in each country come to see that we were working together, side by side, toward the settlement of the centuries-old boundary conflict. Since “one picture is worth a thousand words,” Roger suggested that I arrange for a photograph to be taken of the two presidents. I said that would not be a problem. The media would be present before and after our meeting. Rather than a picture of us shaking hands or standing next to each other, however, Roger wanted us to be sitting, side by side, each with a pen or pencil in his hand, both looking at a map or a pad on which there might be some kind of draft proposal. We would not be looking at the camera or at each other but rather working. Such a photograph might help convince third parties, the media, and the public that things had started to change for the better. The photograph would make clear that the presidents were in a collaborative effort, tackling the boundary problem together. When I returned from Paraguay, I showed Roger a newspaper with a front-page photograph of the two presidents working together (image shown below). I told Roger that I knew the photograph was intended to influence the public. What surprised me was the extent to which the photograph also influenced President Fujimori and me. Looking at the photograph, President Fujimori said that the public in each country would now be expecting us to settle the boundary. We had publicly undertaken that task, and we owed it to the people in each country to succeed. Status: “I’ll Recognize His Seniority” President Fujimori and I met for the first time in Asuncion. We were in the presidential suite kindly offered by the Argentinean President Carlos Menem as a neutral territory. At that time, President Fujimori had been president of Peru for eight years and I had been president of Ecuador for four days. “You can make a first impression only once,” I reminded myself. “Stating the evident will not harm my position. Contrarily, it will convey the image of an open, objective person,” I thought. “I’ll recognize his seniority, a personal matter where there’s no debate, and I will not accept his substantive proposals about delicate matters where there’s a hot debate.” I said, “President Fujimori, you’ve been president for eight years. I’ve been a president for four days. You have negotiated with four of my predecessors. I would like us to benefit from your extensive experience.” I asked him, “Do you have ideas on how we might deal with this border dispute in a way that would meet the interests of both Peru and Ecuador?” This photograph on the front page of an Ecuador newspaper helped change the political climate in 1998 by showing presidents Mahuad of Ecuador and Fujimori of Peru working together side by side. I recognized his seniority with courteous gestures, which were reciprocated by him. For example, I always made sure he entered rooms first as the senior president. In this way, I acknowledged and respected his seniority, a particular status of President Fujimori. I also acknowledged my own particular status as president and as a connoisseur of the Ecuadorian reality. To recognize areas where President Fujimori held high status did not imply that I was agreeing with him or with his position. Contrarily, when combined with showing appreciation, honoring his status gave me room to manifest my openly discrepant standings without endangering the relationship. Autonomy: Do Not Tell Others What to Do Autonomy is a core concern for human beings, particularly sensitive for figures like politicians who are in positions of authority. For many years, Ecuador and Peru refused to negotiate with one another, each fearing that they would be seen as “giving in” to the other’s demands. No politician likes to be seen as a puppet of anybody else, especially when each one is on a different side of a centuries-old conflict. It would be dangerous for a president to do something that would make our constituents suspicious or otherwise put us in a difficult position in our own country. In all our meetings, I was very conscientious to respect his autonomy and to ensure my own. It would have been deadly wrong, for example, to try to tell President Fujimori what to do. Rather I asked for his perceptions and reactions on how we two presidents might best settle this protracted and costly boundary dispute. My personal respect for him did not imply that I was agreeing with him or with his demand. “I simply cannot ask Congress and the people to give in to the demands of Peru. I’m not going to do it. Were I to do it, Congress would never agree; nor would any Ecuadorian. That’s a dead-end road. What are your alternative ideas on how we might move forward toward a peaceful agreement?” I asked President Fujimori to appreciate the fact that the Ecuadorian president, Congress, and people would never concede to this Peruvian claim. Our autonomy would be crushed. Role: “Us” Means “Us” for Both Sides Negotiators play multiple, simultaneous, sometimes contradictory, overlapping, or complementary roles. In an effort to settle this longstanding boundary dispute, each president would have a crucial job. Each would have the task of bringing his own constituents to accept a settlement of the boundary. I saw my role as leading two simultaneous negotiations. One role, obviously, was as negotiator with President Fujimori. The other role, not so obvious but equally important, was my role as a negotiator with the people of Ecuador, its institutions, and representative organizations. I recognized that President Fujimori had the same two roles and faced the same tasks. Therefore, I proposed to him we not do anything to harm each other’s legitimacy as authorized representatives of our peoples. For instance, it would have been self-defeating to claim that a treaty was good for Ecuador because it was bad for Peru—or vice versa. On the contrary, I saw that the role of each president was to demonstrate that an agreement was good for both countries, good for the region, good for trade, good for economic development, and good for the alleviation of poverty. We needed a win-win proposition. In crafting that proposition, our roles were both stressful and full of personal meaning. Too often in international affairs, the goal is seen as obtaining a commitment from the other side. The media keep asking: “Who backed down?” “Who gave in?” “Did you reach an agreement?” “No? So the negotiations failed?” They want to see us playing the role of the victorious hero defeating a deceitful enemy. But “us” means “us” for both sides. In a negotiation, the most useful and powerful outcome may be an emotional commitment to continue working together in order to implement a peace agreement after signing it. Working together did not suggest that either of us gave up our liberty, our discretion, or our autonomy. Rather, we transformed a problem into an opportunity. That required a new conception of the roles we played: a shift from opponents to colleagues, from positional bargainers in a merely distributional zero-sum game to joint problem solvers inventing new options to increase the size of the pie and the scope of possible outcomes. Core Concerns as a Bundle At some moments, the situation called for intertwining different core concerns and reinforcing them at different levels. One particularly challenging circumstance stands out. The nonbinding opinion (Parecer) of the international experts gave a big push to Peru’s claim to Tiwintza. It would have been impossible, however, for any Ecuadorian president to yield to the claim without losing legitimacy, demeaning his presidential status, betraying his role, and risking his people’s appreciation and affiliation. I wanted to recognize the strength and merits of the Peruvian case, and at the same time to get appreciation for the Ecuadorian situation, my autonomy, and my role. My sensitivity to these core concerns helped me navigate this difficult terrain. “President Fujimori,” I said, “Peru has a strong claim to the disputed area. Because of the commission’s Parecer, it may, in fact, be stronger than Ecuador’s claim (appreciating Peru’s point). If I were president of Peru, I’d have no other option than to seek to get every square meter of that land (appreciating merit in Peru’s perspective). Yet, as president of Ecuador, I cannot agree to give Peru territory that every president and every Congress since Ecuador was born has insisted is part of Ecuador. (I was asking him to reciprocate by appreciating my situation and understanding my difficulties.) We are convinced that we have the moral and legal rights over the area in dispute, and we’re not going to change that conviction because of a nonbinding technical opinion (Parecer). One hundred more opinions like that one wouldn’t be sufficient to change our centuries-old feelings of ownership over those territories. (As a country, we have our autonomy.) Hence, any president of Ecuador should say and do what I’m saying and doing. (Asking for his reciprocal affiliation.) Now, in our role as presidents, we can undertake our new mission, which is to find a formula acceptable for the peoples in both countries.” (I was searching for an additional common ground of affiliation in fairness and justice.) This dialogue had the noticeable effect of committing us both to a joint problem-solving approach. Our predominantly rational, carefully prepared, goal-oriented initial steps were additionally fueled by the rapport built rapidly between us and among our delegations. Peace became a flashing beacon, a powerful magnetic force taking up most of our time and energy during my first seventy-seven days in office. THE AGREEMENT We kept the people of Ecuador permanently informed about the advance of our negotiation. As progress was evident, a virtuous circle replaced the old vicious one. Negotiation became popular and openly a part of our national objectives. Participation increased. Everybody wanted to be part of the process and to express their voices. Common goals enhanced trust. Political actors started giving support because they understood gains were larger than risks if they represented the now popular will for peace. Belief in a negotiated solution replaced the usual pessimism. Overwhelming support at all levels of society boosted the government’s initial action plan. Although this peace process did not stabilize the economy, the menace of war no longer worsened the economic situation. On October 26, 1998, in Brasilia, ten weeks after our first meeting, President Fujimori and I signed a final, comprehensive peace treaty that was ratified by the Congress of each country. The two countries agreed that the entire disputed boundary area would become an international conservation park in which there would be no economic or military activities except as the two governments might later agree. Tiwintza itself required special treatment. We two presidents agreed that if the representatives of the four countries that were helping us could concur on a recommendation for Tiwintza, we would commit ourselves to accept it. Congresses of both countries voted to give the representatives authority to arbitrate. A creative agreement for Tiwintza was formulated. The representatives separated sovereignty rights from property rights over Tiwintza. Thus, the land is now within the sovereign territory of Peru. And one square kilometer of land around Tiwintza, just inside Peru and adjoining Ecuador, is now private property owned in perpetuity by the government of Ecuador (just as Ecuador might own some land in Lima, Peru). Neither country “gave up” Tiwintza. The government of Peru can say, “Tiwintza is part of our sovereign territory.” The government of Ecuador can say, “We own Tiwintza forever.” A FINAL REFLECTION I agree with Roger and Dan that negotiators often assume that the best way to negotiate is purely rational. To be sure, strong hostile emotions easily escalate and cause problems. Yet, more importantly, in my experience, emotions can be helpful. When going into negotiations, I was ready to take the initiative and act upon each of the core concerns—on appreciation, affiliation, autonomy, status, and role. In doing so, President Fujimori and I established good rapport, a strong working relationship, and a stable agreement. The Ecuador-Peru negotiations of 1998 were in themselves a complete success. The boundary was settled and has remained so. Not a single border military incident has been reported since that time. Binational trade and cooperation have reached historical records, and peace has been praised, valued, and owned by governments and citizens alike on both sides of the border. My major reason for wanting to establish peace between Ecuador and Peru was to give both countries the benefits that only peace could bring. Additionally, establishing peace with Peru would enable Ecuador to reduce its military budget. Those resources could then be devoted to programs to alleviate poverty. And that is what my administration did after the treaty was signed in 1998. In January 2000, a military-backed coup forced me out of office for reasons too complicated to go into in this document. This fate is one I share with many Latin American presidents. That is part of the official side of the story. On the personal side, Alberto Fujimori and I gradually developed a personal friendship beyond the call of our duties. In March 2004, over a cup of coffee in Tokyo’s Royal Park Hotel, we reflected on the lessons we learned. Alberto said, “Peace is consolidated. Everybody respects it.” In the beginning, few of us believed that peace was possible. Now it was owned by everybody. Alberto and I remembered a conversation we had in Brazil during the peace process. After a press conference, I had told him: “Things are changing. The situation used to be pretty clear: Ecuadorian journalists on one side, Peruvian journalists on the other. Now they’re mixed together. That’s a good omen for the future.” Alberto had said, “Yesterday, while reading an article in a Lima newspaper, I felt as if you and I were on the pro-peace side, facing together some opposition to peace in both countries.” I nodded in agreement. Since the beginning, we had worked together to satisfy our core concerns for affiliation, appreciation, and autonomy. Our status was respected. And our roles were fulfilling. We had created an atmosphere to advance substantive content. As almost always happens, process and substance walked hand in hand.
Subscribe to:
Posts (Atom)